The expense of down can vary from $2 stresser dollars from grey duck feathers to $50 per pound for 800 fill power white goose down. Multitudes of requests are sent simultaneously for the targeted resource, making it virtually impossible for your resource to deliver normal services towards the legitimate users. The assaults were released by hacktivists supporting WikiLeaks in response to suspension of solutions by these firms to WikiLeaks.
Do not get too excited yet. The compromised systems, called zombies are then instructed to attack for the targeted resource. Regulations only provide stresser for your minimum security requirements. There are several approaches which can stresser help to prevent a DDoS attack.
Never forget to use a Firewall. Distributed denial-of-service attacks can paralyze any type of network for days, freezing online services and crippling a company\'s status. Adopt two factor authentication (2FA).
The actual procedure for separating down and feathers necessitates the use of an air blower that pushes the filling through a number of walls. Try having minimum of two machines so as tot escape single point failure while you\'re running multi homed hosting. DDoS attackers are taking advantages of internet\'s package data technology in which the data transferred from any source to any destination. Try having minimum of two machines so as tot escape single point failure while you\'re running multi homed hosting. Also, make positive changes to password at least every fortnight.
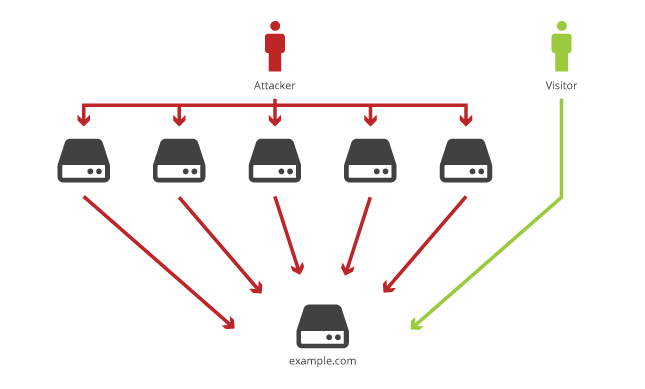
The actual procedure for separating down and feathers involves the use of an air blower that pushes the filling through a group of walls. The compromised systems, called zombies are then instructed to attack to the targeted resource. DDoS attackers are taking benefits of internet\'s package bandwith technology in which the data transferred from any source ddos to any destination. IT security apparatus has to be regularly evaluated and modernized in tune with ations in threat scenario.
Do not get too excited yet. K) together with other European countries have initiated investigation right right into a collection of dispersed denial of program (DDoS) assaults that disrupted web sites of Amazon, PayPal, MasterCard, VISA and PostFinance and many other individuals. Regulations only provide for the minimum security requirements. It also contributes to serious crimes like identity theft, phishing, stealing your credentials and gaining illegal use of your bank accounts and stealing your hard-earned money.
Many consumers confuse down and feathers as being the same, but that is a false comparison because of the means by which both fillings behave. It also cannot protect against major attacks, especially when it is still in the analyzing page. DDoS attackers are taking benefits of internet\'s package bandwith technology the location where the data transferred from any source to any destination. Don\'t select free versions. Depending on its use, it can stresser be great and bad.
Never forget to make use of a Firewall. If more than one machine is connected on the same LAN, utilize the LAN private IP addresses to communicate between the machines. Therefore, it is quite important to hold the DOS protection you will need because it becomes easier and simpler for criminals to hold out DDOS attacks.
Tidak ada komentar:
Posting Komentar